Which of the Following Suggestions Can Help Prevent Vlan Hopping Attacks on a Network?
Nosotros'll start with a few concepts:
VLAN
A virtual local expanse network (VLAN) is used to share the physical network while creating virtual segmentations to divide specific groups. For case, a host on VLAN ane is separated from whatever host on VLAN two. Any packets sent between VLANs must go through a router or other layer iii devices. Security is ane of the many reasons network administrators configure VLANs. However, with an exploit known as 'VLAN Hopping', an assaulter is able to bypass these security implementations. Larn more near network partition and VLANs here.
VLAN Hopping
This type of exploit allows an attacker to bypass whatsoever layer 2 restrictions built to divide hosts. With proper switch port configuration, an attacker would take to get through a router and any other layer three devices to access their target. Nevertheless, many networks either accept poor VLAN implementation or have misconfigurations which volition allow for attackers to perform said exploit. In this article, I will go through the two primary methods of VLAN hopping, known as 'switched spoofing', and 'double tagging'. I will then discuss mitigation techniques.
Switched Network
It is crucial we understand how switches operate if nosotros would similar to find and exploit their vulnerabilities. Nosotros are not necessarily exploiting the device itself, merely rather the protocols and configurations instructing how they operate.
On a switch, a port is either configured as an access port or a trunking port. An access port is typically used when connecting a host to a switch. With the implementation of VLANs, each access port is assigned to only i VLAN. A trunking port is used when connecting two switches or a switch and a router together. Trunking ports allow for traffic from multiple VLANs. A trunk port can be configured manually or created dynamically using Dynamic Trunking Protocol (DTP).
DTP is a Cisco proprietary protocol where one use is to dynamically constitute a trunk link betwixt two switches.
Switched Spoofing VLAN Set on
An attacker acts as a switch in social club to play tricks a legitimate switch into creating a trunking link between them. Every bit mentioned before, packets from any VLAN are allowed to pass through a trunking link. Once the trunk link is established, the attacker and so has admission to traffic from whatever VLAN. This exploit is only successful when the legitimate switch is configured to negotiate a torso. This occurs when an interface is configured with either "dynamic desirable", "dynamic auto" or "torso" mode. If the target switch has i of those modes configured, the attacker then tin generate a DTP bulletin from their computer and a torso link can exist formed.
Double Tagging
Double tagging occurs when an assaulter adds and modifies tags on an Ethernet frame to allow the sending of packets through whatever VLAN. This attack takes reward of how many switches process tags. Most switches volition only remove the outer tag and forward the frame to all native VLAN ports. With that said, this exploit is simply successful if the attacker belongs to the native VLAN of the trunk link. Some other important signal is, this set on is strictly one way as it is impossible to encapsulate the return packet.
VLAN Hopping Exploit
Scenario one - Switch Spoofing Assail
In this scenario there exists the assailant, a switch, and the target server. The attacker is attached to the switch on interface FastEthernet 0/12 and the target server is attached to the switch on interface FastEthernet 0/11 and is a office of VLAN 2. Take a expect at the following topology.
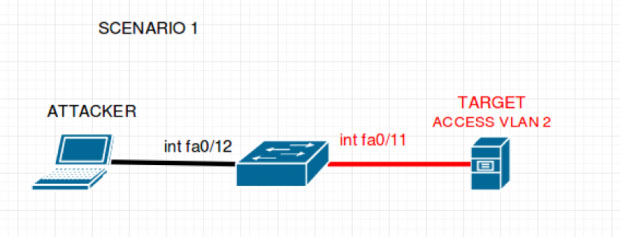
Once you are familiar with the topology, accept a look at a few of the configurations set for the switch:
interface FastEthernet0/11
switchport mode access
switchport mode nonegotiate
switchport access vlan ii
!
interface FastEthernet0/12
switchport mode dynamic machine
Hopefully, you can meet the configuration issue with interface fa0/12. This port is fix to have incoming negotiations to decide whether the port is for admission or trunking. Which means an assaulter is able to perform a Switch Spooking assail. One time the attacker connects to the port they can so send a DTP bulletin and a trunking link will be established.
An assailant can use the plan Yersinia to craft and send a DTP message. Yersinia is a penetration testing framework built to assault many protocols that reside on layer 2. It comes pre-installed with kali Linux and has an easy to apply graphical user interface (GUI).
Yersinia Homepage - http://www.yersinia.cyberspace/
To launch Yersinia:
yersinia -Grand
Here is a quick look at the GUI:
Now to send a DTP bulletin is as simple equally the following 4 steps:
- click "Launch assail"
- click the tab "DTP"
- click "enable trunking"
- click "ok"
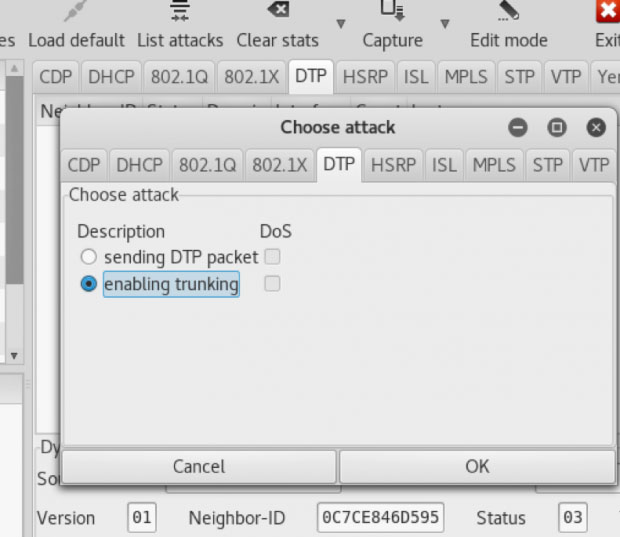
Yersinia will the send out a DTP message and inside a few seconds, a trunking link will be established. In our scenario, the attacker will then have access to all traffic flowing through VLAN 2 and can directly attack without going through any layer 3 devices.
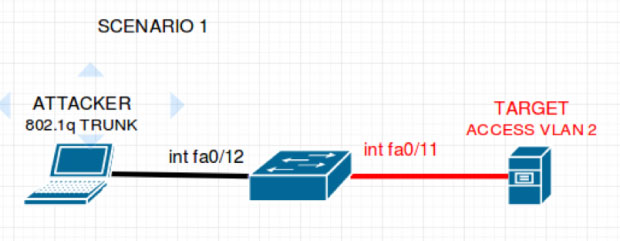
Scenario ii - Double Tagging Attack
In this scenario, in that location exists an assaulter, 2 switches, and a target server. The attacker is fastened to switch one. Switch i is attached to switch two and finally, our target is attached to switch two. Take a look at the post-obit topology.
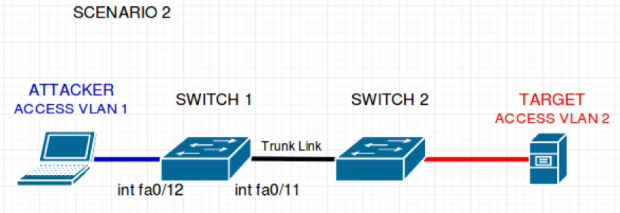
Once y'all are familiar with the topology, have a look at a few of the configurations set for switch one.
interface FastEthernet0/12
switchport fashion access
switchport nonegotiate
switchport access vlan ane
!
interface FastEthernet0/11
switchport trunk encapsulation dot1q
switchport fashion torso
switchport nonegotiate
switchport trunk native vlan i
From these configurations, we meet that an attacker would be unable to perform a switch spoofing attack. Yet, we see that the assailant belongs to the native VLAN of the trunk port. Which means this topology is vulnerable to a Double Tagging attack.
An attacker can use the program Scapy, to create the specially crafted frames needed for processing this set on. Scapy is a Python program created to dispense packets.
Scapy Homepage - https://scapy.net/
Scapy Documentation - http://scapy.readthedocs.io/en/latest/usage.html
Get-go Scapy:
sudo ./scapy
Using the sendp() role to craft a packet:
>>>sendp(Ether()/Dot1Q(vlan=1)/Dot1Q(vlan=2)/IP(dst='
This volition generate a double 802.1q encapsulated bundle for the target on VLAN two. Take a look at the post-obit topology to view how the switches manage this frame.
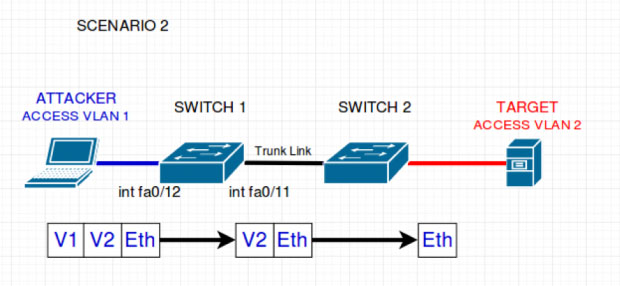
From the picture, we tin see that switch ane reads and removes only the outside tag. It checks that the host is role of the stated VLAN and forwards the packet to all native VLAN ports (VLAN one). Switch ii and then receives the packet with simply ane header left. It assumes the frame belongs to the stated VLAN on this tag (VLAN 2) and forwards to all ports configured for VLAN 2. The target so receives the bundle sent by the attacker.
VLAN = HOPPED.
Due to the nature of this set on, information technology is strictly one way. Delight also note that this assail may not piece of work on new switches.
Mitigation for VLAN Hopping
Switched Spoofing
To prevent a Switched Spoofing assail, there are a few steps you should have:
- Practise not configure any access points with either of the following modes: "dynamic desirable", "dynamic motorcar", or "body".
- Manually configure access ports and disable DTP on all access ports.
switchport mode admission
switchport mode nonegotiate - Manually configure all trunk ports and disable DTP on all trunk ports.
switchport mode trunk
switchport mode nonegotiate - Shutdown all interfaces that are non currently in employ.
Double Tagging
To prevent a Double Tagging assault, keep the native VLAN of all trunk ports different from user VLANs.
Last Note
Switches were not built for security. Nevertheless, it is important to utilise security measures at every level. If you are to take the fourth dimension to segment your network, make sure it is washed properly and securely. Be diligent when configuring your network.
muellerraingerred.blogspot.com
Source: https://cybersecurity.att.com/blogs/security-essentials/vlan-hopping-and-mitigation
0 Response to "Which of the Following Suggestions Can Help Prevent Vlan Hopping Attacks on a Network?"
Post a Comment